Jam.py documentation
Sanitizing¶
To prevent Cross Site Scripting (XSS) attacks, Jam.py sanitizese field values displayed in the table columns.
For example, if field contains the following text:
"<span style='color: red'>USA</span>"
when unsanitized it will be displayed in the table column as follows:

When the field text sanitized, it is transformed to the following:
"<span style='color: red'>USA</span>"
as you can see symbols ‘<’ and ‘>’ are replaced with ‘<’ and ‘>’ and the table column will be displayed this way:
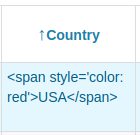
There are two ways to prevent sanitizing.
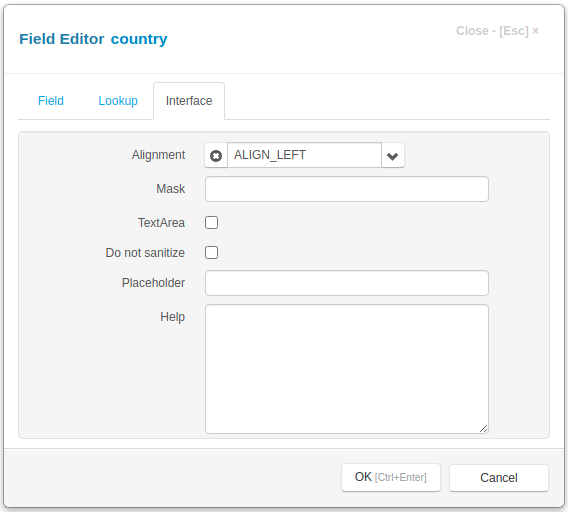
First is to set Do not sanitize attribute in the Interface tab in the Field Editor Dialog
Second is to write the on_field_get_html event handler. If the this event handler returns a value it is not sanitized.